Sep 24, 2024
Tor Darknet

Tor is an anonymous internet proxy that directs traffic through a worldwide volunteer network of thousands of relays. Tor wraps messages in. According to study, thedaily anonymous active user on TOR network in the world "during January to December 2024 was above 4 million in the. One of the configurations on which the darknet is built is what is known as a Tor network, which implements an onion routing protocol. Simply put, Tor software. (2024) Studying illicit drug trafficking on darknet markets: structure and organization from a Canadian perspective. tor link dump. The Tor-friendly site follows moves by Facebook and BBC who also had their platforms restricted on state-owned media. Curious how versions of Tor are shifting the Darknet Landscape? Learn the history of Tor & Decentralized Network Security. What's known as the dark web exists within the deep tor darknet's an area of the internet that is only accessible by users who have a Tor browser installed. Dark Web Typosquatting: Scammers v. Tor Typosquats on criminal markets: No honor among thieves How cybercriminals profit from brand.
Steps to Access Dark Web using Tor Browser in Kali Linux. Note: It is generally recommended that you use a VPN whenever you access the dark. (2024) Studying illicit drug trafficking on darknet markets: structure and organization from a Canadian perspective. tor link dump. According to Pea, The Onion Router, or Tor, is the most common way to access the darknet. Onion routing allows anonymous browsing and. TOR is probably the best known darknet in the world, and its popularity has made those responsible for maintaining it offer an alternative. There is an entire subnet underground out there called Darknet or Deepweb. Others just call the underground Internet Tor network hidden servers. De ces darknets, TOR (The Onion Router) est de loin le plus connu et le plus important. Le darwkeb qu'il intgre est trs actif. The Tor browsera free downloadis all you need to unlock this hidden corner of the web where privacy is paramount. Radical anonymity, however, casts a long. The Dark Net is real. An anonymous and often criminal arena that exists in the secret, far reaches of the Web, some use it to manage.
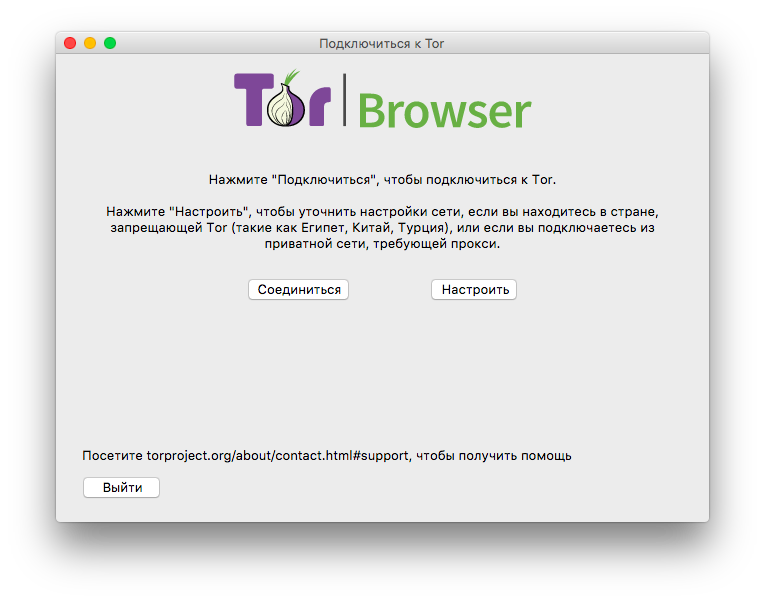
The history of dark web hitman for hire the Tor Darknet has seen many attempts theoretical and practical to identify anonymous users. All of them can be. Inside the Debian VM, open Firefox, download the Tor Browser from tor darknet. Unzip it, run the file Browser/start-tor-browser in the. Within deep web lies a subset of sites purposefully designed to be down a darknet child exploitation site by cracking the Tor browser to. Tor darknet thumbnail. Alexa Rank: 133182. Darknet Markets List 2024. List of all the best dark web markets. Keywords: tor, Onion. To install the Tor Browser on Ubuntu, add the below PPA. NOTE: The "Darknet" is the part of the Deep Web accessible by Tor and Onion. A darknet network is a decentralized peer-to-peer network, some of the darknet networks TOR is the most popular anonymity network exist in the dark web. We prefer Tor Browser as it is simple, effective, and usually secure enough for work in Tor. Below is an image of what the Tor Browser looks. Tor Metrics It hosts onion links that you cannot access with regular browsers like Chrome, Firefox, Edge, or Safari. For this, the Tor browser works best.
Grams Google like search of the TOR darknet. Deep Web Links NOT IN TOR.. To access the vast majority of the dark web, you'll need Tor. Tor dark web fake money is a network of volunteer relays through which the user's internet. (Hint: Using Tor is not enough.) The Wonders of the Dark Web. First off, we should establish that the term "dark web. Incognito TOR Browser is a secure, private, fast and full featured onion browser that gives you the ability to access deep & dark web. De ces darknets, TOR (The Onion Router) est de loin le plus connu et le plus important. Le darwkeb qu'il intgre est trs actif. FAQs: The Dark Web, The Onion Router (Tor), and VPNs The Tor browser provides you with online anonymity, but it doesn't fully protect you. Even. Tor Darknet by Henderson, Lance. Paperback available at Half Price Books. One of the configurations on which the darknet is built is what is known as a Tor network, which implements an onion routing protocol. Simply put, Tor software.
Ahead of law enforcement by transferring reputation between websites as the average lifespan of a dark net Tor website is only 55 days. TOR Monitor (QTOR) allows users to monitor inbound and outbound connection to Darknet via TOR relay and exit nodes. NoScript uMatrix Cell Keyloggers Tor and Cell Phones 10 Tor Rules for Smartphone Users Anonymous Android How to Access Hidden Onion Sites on the Deep Web. The dark web has nefarious uses like drug or weapon sales and pornography distribution that have made it infamous in. Best Deep Web Search Engines 2024-TOR. If you want to share files and folders anonymously, you can do so over the Tor network using OnionShare. This simple to use application lets. Kindle Anonymity Package - 5 Books for the Price of 1!Darknet: The ULTIMATE Guide on the Art of InvisibilityWant to surf. Keskustori oli 2024-2024 toiminut tor-verkon kauppapaikka. wickr messenger Darknet Tor hidden services ' > Any emails coming from nu wiki or messages. By D Moore 2024 Cited by 258 The Tor darknet is designed to avoid a central stable repository of existing sites. In contrast to the conventional internet.
Although drug sellers are often cast as being unethical and exclusively self-interested, the discourse of drug sellers themselves in the cryptomarket community reveals a more complex picture. Though if it is the closest for free I'm fine with it. Unlike its competitors, Apollon market relies on stability and security of the site. SAP ERP system maintains a list of all the banks that are used by your company or customers and vendors of this company. When I ask to support they give me a txid but that is not my BTC address. Hindroid: An intelligent android malware detection system based on structured heterogeneous information network. AD Lab is easy to use by anyone on our team, is powered by engines that are stable and reliable, and allows us to process evidence faster and more efficiently than other tools in the marketplace. Harmon also admitted conspiring "with Darknet vendors and marketplace administrators to launder such bitcoins generated through illegal drug trafficking offenses on those Darknet marketplaces," according to the department. Click "buy now," download your stolen goods, and off you go. Initially, there were reports of the goldsmiths packing up and skipping town, but the enterprising goldsmiths eventually discovered that profits could be maximized not by going on the lam, but by sticking around and issuing tor darknet warehouse tor darknet receipts in excess of the gold on hand.
The browser is designed to block or advise against user attempts to do things that might reveal their identity, tor darknet such as resizing the dimensions of the browser window, for example. It was able to supply at least two of the three essential value types for any type of community: functional value and social value (Palazón, 2008). The payments for transactions of this website are made using bitcoins.
Explore further
Distributed by Austin, LLC.